In today's digital landscape, Distributed Denial of Service (DDoS) attacks remain one of the most significant threats to online services. Anycast networks have emerged as a powerful defense mechanism against these attacks, offering both performance benefits and robust security. Let's explore how DDoS protection works within an anycast network architecture.
Understanding Anycast Networks
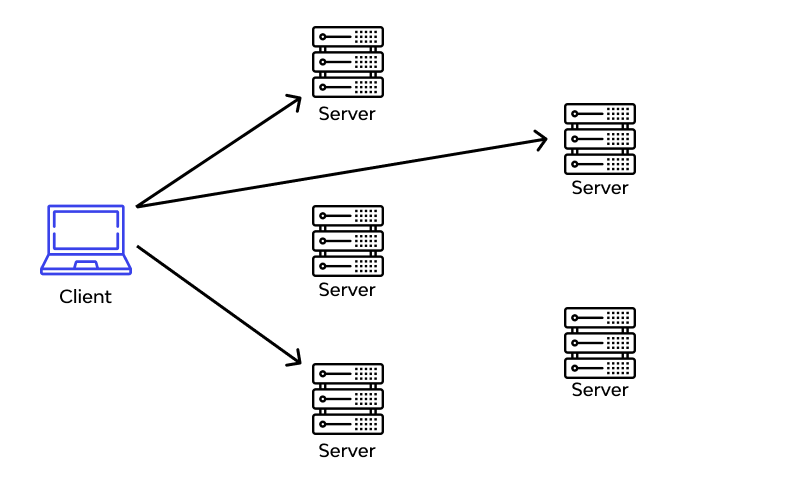
Before diving into DDoS protection, it's crucial to understand what makes anycast networks unique. Unlike traditional unicast routing, where each destination IP address identifies a single endpoint, anycast allows multiple endpoints (nodes) to advertise the same IP address. When a client attempts to connect, the network automatically routes their traffic to the nearest available node.
The Fundamentals of Anycast DDoS Protection
1. Traffic Distribution by Design
Anycast's primary defense mechanism against DDoS attacks lies in its inherent architecture. When an attack occurs:
- Attack traffic naturally spreads across multiple data centers
- Each location handles only a fraction of the total attack volume
- Network capacity multiplies with each additional point of presence (PoP)
2. BGP Routing Magic
Border Gateway Protocol (BGP) plays a crucial role in anycast DDoS protection:
- Each anycast node announces the same IP range to the internet
- Internet routers automatically select the shortest path
- During attacks, traffic automatically redistributes if a node becomes overwhelmed
Advanced Protection Mechanisms
Intelligent Traffic Scrubbing
Modern anycast networks employ sophisticated traffic analysis:
-
Real-time Pattern Recognition
- Behavioral analysis of incoming traffic
- Identification of attack signatures
- Distinction between legitimate and malicious requests
-
Multi-layer Filtering
- Layer 3/4 protection against volumetric attacks
- Layer 7 filtering for application-layer attacks
- Protocol-specific defenses
Dynamic Capacity Adjustment
Anycast networks can respond to attacks by:
- Automatically scaling network capacity
- Adjusting routing policies in real-time
- Implementing rate limiting at edge locations
Real-world Implementation
Let's look at how this works in practice:
Normal Traffic Flow:
Client Request → Nearest Anycast Node → Origin Server
↑
BGP selects optimal path
During DDoS Attack:
Attack Traffic → Distributed across all nodes
→ Filtered at each location
→ Only clean traffic reaches origin
Key Components
-
Edge Nodes
- Distributed globally
- Each capable of filtering attacks
- Redundant capacity for surge protection
-
Traffic Analysis Systems
- Machine learning-based threat detection
- Historical pattern analysis
- Real-time traffic scoring
-
Control Plane
- Centralized management
- Dynamic policy updates
- Automated response mechanisms
Best Practices for Implementation
To maximize DDoS protection in an anycast network:
-
Strategic Node Placement
- Deploy nodes in major internet exchanges
- Ensure geographic diversity
- Consider traffic patterns and user distribution
-
Capacity Planning
- Maintain significant headroom at each location
- Regular capacity assessments
- Predictive scaling based on traffic patterns
-
Monitoring and Analytics
- Implement comprehensive logging
- Real-time visibility across all nodes
- Regular performance analysis
The Future of Anycast DDoS Protection
As threats evolve, anycast networks continue to advance:
- Integration of AI/ML for better threat detection
- Enhanced automation in response mechanisms
- Improved traffic analysis capabilities
Conclusion
Anycast networks provide a robust foundation for DDoS protection through their distributed nature and intelligent traffic management capabilities. By combining this architecture with advanced filtering mechanisms and dynamic response systems, organizations can build resilient infrastructure capable of withstanding modern DDoS attacks.
The key to success lies in proper implementation, regular maintenance, and continuous monitoring of the network's security posture. As attack vectors evolve, anycast networks' ability to adapt and distribute load makes them an increasingly valuable tool in the cybersecurity arsenal.
Remember: DDoS protection is not a one-time setup but a continuous process of improvement and adaptation. Regular testing, updating, and optimization of your anycast network's security measures are essential for maintaining effective protection against evolving threats.